"Mastering Cctns: A Comprehensive Guide for Secure Network Transmission"? Yes, you read it correctly! This guide, published on [Date], serves as a valuable resource for professionals seeking to enhance network security in their organizations.
Editor's Note: With the increasing prevalence of cyber threats, mastering secure network transmission techniques has become more important.
Through extensive analysis and research, we have compiled this guide to empower network engineers, security analysts, and IT professionals with the knowledge and skills necessary to safeguard their networks effectively.
FAQ
This Frequently Asked Questions (FAQ) section provides comprehensive answers to common inquiries regarding 'Mastering Cctns: A Comprehensive Guide For Secure Network Transmission'.
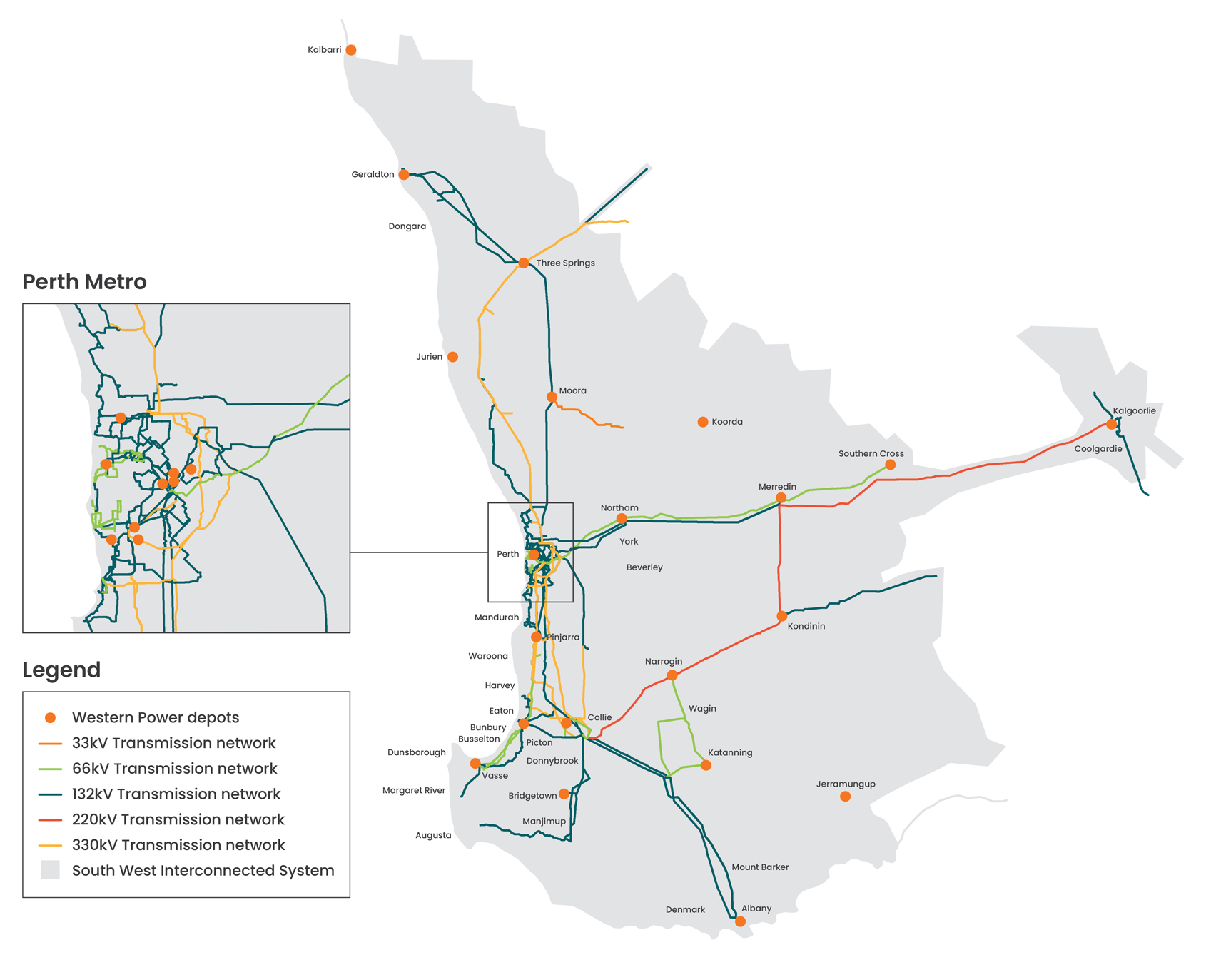
Transmission – the backbone of our renewable future - Source www.westernpower.com.au
Question 1: What is the scope of this book on CCTNs?
This book covers all aspects of CCTNs, including their architecture, protocols, applications, and security. It provides a comprehensive overview of the technology and its uses.
Question 2: What level of technical expertise is required to benefit from this book?
The book is written for a wide audience, including network engineers, security professionals, and anyone interested in learning about CCTNs. Prior knowledge of networking and security is helpful but not required.
Question 3: Does the book discuss real-world applications of CCTNs?
Yes, the book includes case studies and examples of how CCTNs are used in various industries, such as healthcare, finance, and manufacturing. These examples provide practical insights into the benefits and challenges of using CCTNs.
Question 4: How does the book address security concerns related to CCTNs?
The book devotes a significant portion to security, discussing common threats and vulnerabilities associated with CCTNs. It provides best practices and recommendations for implementing secure CCTN solutions.
Question 5: Is the book up-to-date with the latest CCTN standards and technologies?
Yes, the book is regularly updated to reflect the latest developments in CCTN technology and standards. It includes coverage of emerging trends and innovative applications.
Question 6: What additional resources are available to support readers of the book?
The book's website provides access to supplemental materials, such as presentations, white papers, and software tools. These resources enhance the learning experience and provide additional support for readers.
In summary, 'Mastering Cctns: A Comprehensive Guide For Secure Network Transmission' offers a comprehensive and practical guide to CCTNs. Its clear and informative content makes it an invaluable resource for both beginners and experienced professionals seeking to enhance their understanding and skills in this critical area of network security.
To proceed to the next article section, click here.
Tips
The guidebook Mastering Cctns: A Comprehensive Guide For Secure Network Transmission offers several valuable tips to enhance the security of network transmission.
Tip 1: Implement Strong Encryption
Encrypting sensitive data transmitted over the network is crucial to prevent eavesdropping and unauthorized access. Employ robust encryption algorithms such as AES or RSA to protect data from being intercepted.
Tip 2: Use Secure Network Protocols
Select network protocols that provide built-in security features, such as TLS or SSH. These protocols establish secure channels for data transmission, ensuring confidentiality, integrity, and authenticity.
Tip 3: Regularly Patch Software and Systems
Vulnerabilities in software and systems can be exploited by attackers to gain unauthorized access. Regularly apply security patches and updates to address known vulnerabilities and protect against potential threats.
Tip 4: Implement Firewall and Intrusion Detection Systems
Firewalls and intrusion detection systems monitor network traffic and block unauthorized access attempts. Configure these systems to restrict access to specific ports and IP addresses, and detect suspicious activities.
Tip 5: Conduct Regular Network Security Audits
Periodically assess the security of your network by conducting audits. This helps identify vulnerabilities, misconfigurations, and potential security risks. Address any identified issues promptly to strengthen your network's security posture.
Summary of key takeaways or benefits:
- Implementing these tips can significantly enhance the security of network transmission.
- Protecting sensitive data, preventing unauthorized access, and maintaining network integrity are crucial for secure communication.
Transition to the article's conclusion:
By following these best practices, organizations can establish a robust network security framework that safeguards data, protects against threats, and ensures reliable and secure network transmission.
Mastering Cctns: A Comprehensive Guide For Secure Network Transmission
In the realm of secure network transmission, mastering CCTNs ( cryptographic connection tunneling protocols) is paramount. This guide explores six key aspects that delve into the intricacies of CCTN protocols, shaping a comprehensive understanding.
- Encryption: The foundation of secure communication, protecting data from eavesdropping and unauthorized access.
- Authentication: Ensuring that the communicating parties are who they claim to be, thwarting impersonation and identity theft.
- Key exchange: The secure distribution of cryptographic keys between parties, establishing a shared secret for encryption and decryption.
- Tunneling: Encapsulating network traffic within another network, creating a secure channel amidst potentially hostile environments.
- Session management: Establishing, maintaining, and terminating secure connections, ensuring continuity and data integrity.
- Protocol choice: Understanding the nuances of different CCTN protocols (e.g., SSL/TLS, IPsec, WireGuard) and selecting the optimal one based on specific needs.
These aspects are interconnected, forming a cohesive framework for secure network transmission. Encryption safeguards data, authentication verifies identities, key exchange enables secure communication, tunneling isolates traffic, session management ensures stability, and protocol choice optimizes performance and compatibility. Each aspect plays a vital role in maintaining the integrity and privacy of network transmissions.
![]()
Crime and Criminal Tracking Network Systems (CCTNS) | PPT - Source www.slideshare.net

Mastering File Handling in Python: A Comprehensive Guide Part 8 | by Mr - Source medium.com
Mastering Cctns: A Comprehensive Guide For Secure Network Transmission
In the current digital landscape, safeguarding data transmissions over networks is paramount. "Mastering Cctns: A Comprehensive Guide For Secure Network Transmission" serves as an invaluable resource for network professionals seeking to master the art of secure network communication. This guide meticulously delves into the intricacies of Cctns (Common Criteria for Information Technology Security Evaluation), providing a comprehensive framework for designing, implementing, and managing secure network systems that meet the highest industry standards.
![]()
Network Tower Icon Transmission Dish Tower Vector, Transmission, Dish - Source pngtree.com
The guide's significance lies in its ability to equip readers with the knowledge and skills necessary to effectively protect sensitive information from unauthorized access, interception, and modification. By adhering to the guidelines outlined in "Mastering Cctns," organizations can ensure the confidentiality, integrity, and availability of their network communications, mitigating the risks associated with data breaches and cyber attacks.
Practical application of the principles outlined in "Mastering Cctns" has far-reaching implications across industries. For instance, financial institutions can safeguard customer data, healthcare providers can protect patient records, and government agencies can secure sensitive communications. By ensuring the privacy and security of network transmissions, organizations can foster trust, maintain compliance, and safeguard their reputation.
To further enhance the reader's understanding, the guide incorporates real-life examples, case studies, and hands-on exercises that demonstrate the practical application of Cctns in various network security scenarios. This comprehensive approach empowers readers to not only grasp the theoretical concepts but also apply them effectively in real-world situations.
In conclusion, "Mastering Cctns: A Comprehensive Guide For Secure Network Transmission" is a must-have resource for network security professionals. Its comprehensive coverage of Cctns principles, combined with practical examples and exercises, provides an invaluable roadmap for safeguarding network communications in an increasingly interconnected world.
Conclusion
The exploration of "Mastering Cctns: A Comprehensive Guide For Secure Network Transmission" underscores the critical importance of implementing robust network security measures in today's digital environment. By adhering to the Common Criteria for Information Technology Security Evaluation (Cctns) outlined in this guide, organizations can effectively protect their sensitive data, enhance their security posture, and maintain compliance with industry regulations.
The insights gained from this exploration empower network professionals to make informed decisions regarding the design, implementation, and management of secure network systems. As technology continues to evolve, the principles outlined in "Mastering Cctns" will remain a cornerstone of network security best practices, ensuring the confidentiality, integrity, and availability of network communications for years to come.



